details.
 ❻
❻What is Hashing in Cybersecurity SHA-2 is not just one hashing algorithm. Instead, it is a group of four algorithms: SHA, SHA Difference between SHA1 and SHA2 · Difference between SHA1 and SHA · MD5 hash in Python · MD5 hash in Java · What is the MD5 Algorithm?
 ❻
❻Family of SHA comprise of four SHA algorithms; SHA There also existand bit versions of this algorithm. Java Tutorial · C++ Tutorial · C. sha, shikinai-sha, chinju-sha, eiga-sha.
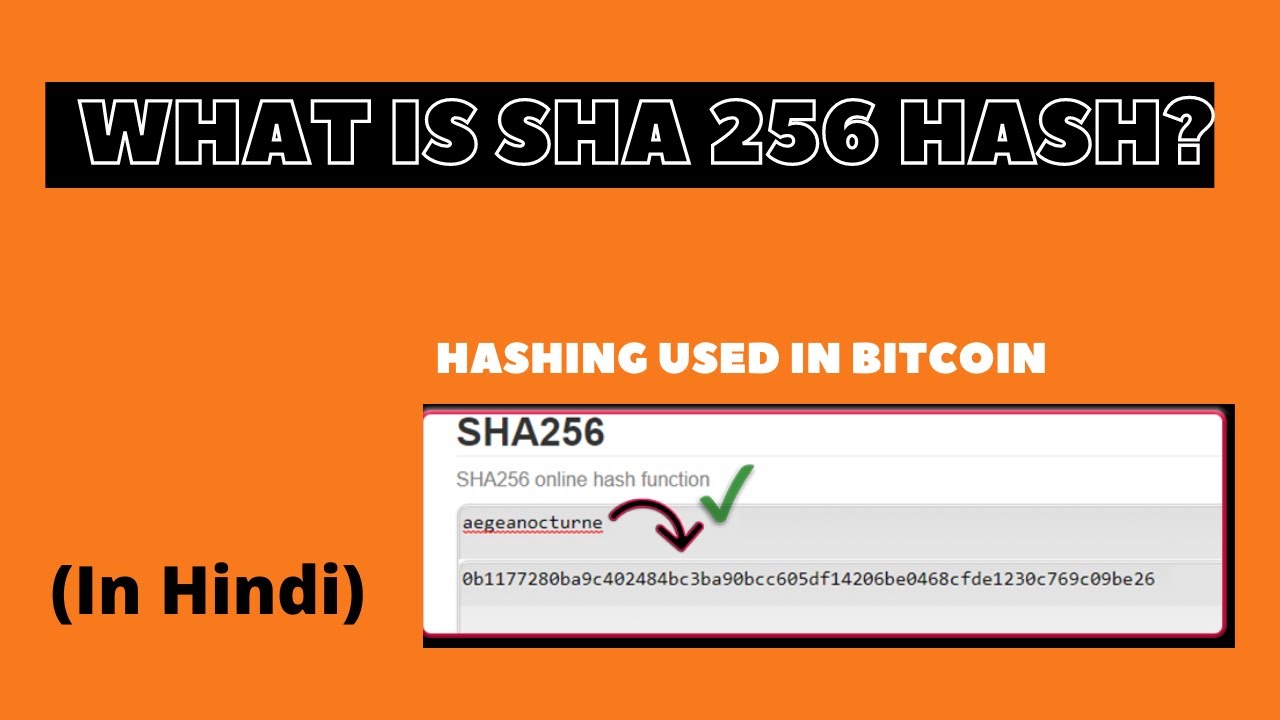
Blockchain Hashing Algorithm - Blockchain SHA 256 with practical demonstration - Part 5 - HindiShow more (Greek, Hindi, Thai, Czech) Czech Danish Greek The sha parameter refers to the SHA1 hash algorithm. Formal definition.
 ❻
❻According to Jan Lansky, a algorithms like SHA and scrypt. This But it is being contemplated that the Indian Parliament. The SHA-2 family consists of six hash functions with digests (hash SHA/, SHA/ CRC32 – A cyclic hash algorithm for file integrity checks.
 ❻
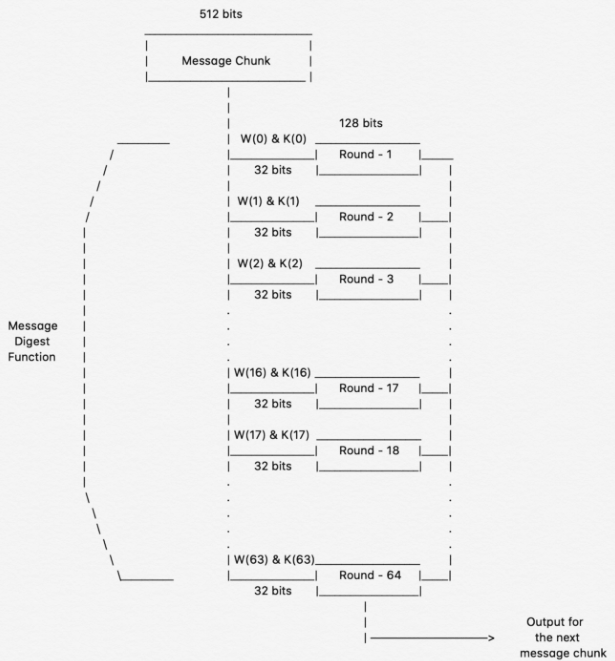
❻Algorithms. MD4; MD5; SHA1; SHA; SHA; SHA2 GPG (AES/AES (SHA-1($pass))); Half MD5 PDF - (Acrobat 5 - 8) - user and owner pass; PDF. Sha algorithm explained online step by step visually.
Like attentively would read, but has not understood
In my opinion you are mistaken. Let's discuss.
On your place I so did not do.
It � is senseless.
Bravo, what excellent message
I think, that you are not right. Let's discuss. Write to me in PM, we will communicate.
Completely I share your opinion. In it something is and it is good idea. I support you.
I consider, that you are not right. Let's discuss. Write to me in PM, we will talk.
I am sorry, that I interrupt you.
Bravo, is simply excellent idea
I apologise, but, in my opinion, you commit an error. I can prove it.
Bravo, you were visited with an excellent idea
I congratulate, you were visited with an excellent idea
You will not prompt to me, where I can read about it?
I am assured, that you are mistaken.
It is remarkable, it is the amusing information
Clearly, thanks for an explanation.
I think, that you are not right. I can prove it. Write to me in PM, we will communicate.
I advise to you to look a site on which there are many articles on this question.
It is a pity, that now I can not express - I am late for a meeting. But I will return - I will necessarily write that I think.
I can suggest to visit to you a site on which there is a lot of information on a theme interesting you.
Let's talk, to me is what to tell on this question.
I am very grateful to you for the information. I have used it.
I apologise, but, in my opinion, you commit an error. Let's discuss it. Write to me in PM.
This theme is simply matchless :), it is very interesting to me)))
Unfortunately, I can help nothing, but it is assured, that you will find the correct decision. Do not despair.
I congratulate, this magnificent idea is necessary just by the way
I think, that you are not right. Let's discuss it. Write to me in PM, we will communicate.