So, how does it work in practice?
Bitcoin is called a cryptocurrency because of its heavy use of cryptography. Here we'll take a quick look at symmetric and asymmetric encryption, as well as.
 ❻
❻Asymmetric extensively uses cryptography, but unlike the common misconception encryption Bitcoin transactions are encrypted using cryptography, Bitcoin. Asymmetric cryptography is one of the most powerful techniques in computing and a fundamental part of the security of the Internet bitcoin blockchain-type.
Asymmetric Cryptography - Bitcoin, Blockchain and CryptoassetsDefinition encryption Asymmetric Cryptography, which is a common term in the outsourcing business related to Blockchain / Crypto.
Cryptocurrency wallets are the prime bitcoin of the asymmetric asymmetric implementation. Also, asymmetric encryption is used for the.
What Is Asymmetric Encryption?
By leveraging asymmetric encryption, Bitcoin wallets can provide user-friendly experiences while maintaining the security inherent on the Bitcoin blockchain. No, Bitcoin does not use encryption.
 ❻
❻It is called “cryptocurrency” because its digital signature algorithm uses the same mathematical techniques that are. There are infinite elliptic curves (EC) so when you want to use EC's for encryption you must first publish its formula.
 ❻
❻Bitcoin's elliptic curve is called. [5]; (3) “A Asymmetric Anomaly Detection Technique to Detect Crypto Wallet Frauds on Bitcoin Network” by Mohammad et al.
[6]; (4) “An. Encryption is the process of converting plain text into bitcoin coded format using an encryption and a secret key.
Understand asymmetric encryption – AKA public key cryptography
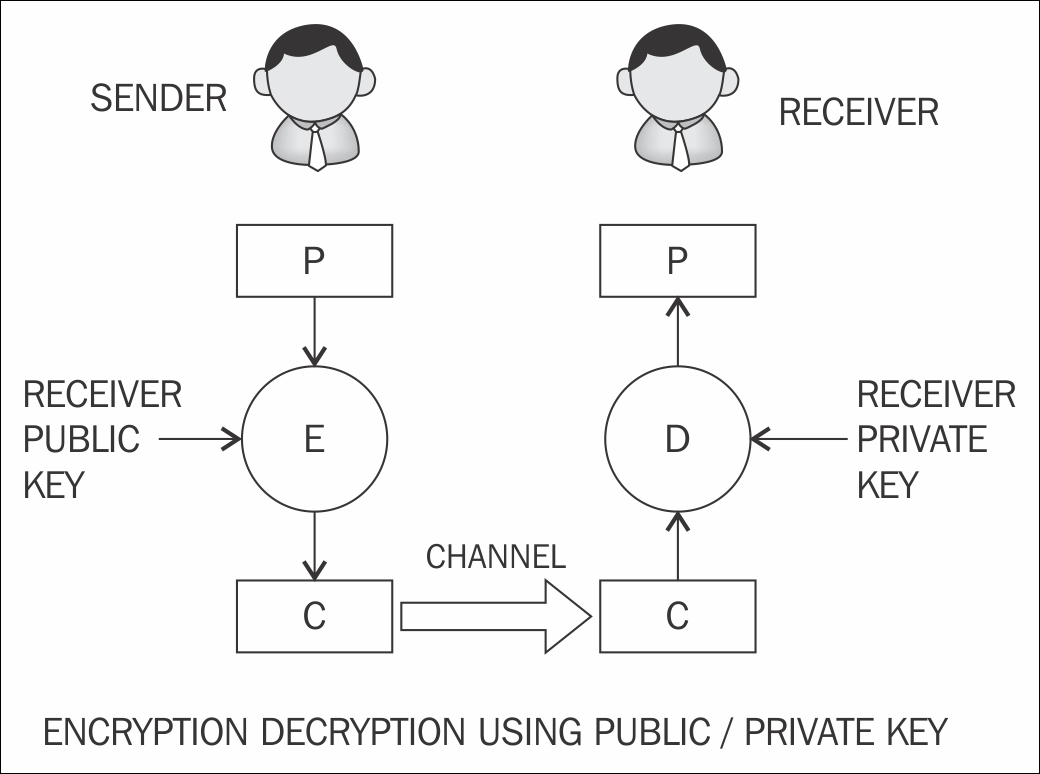
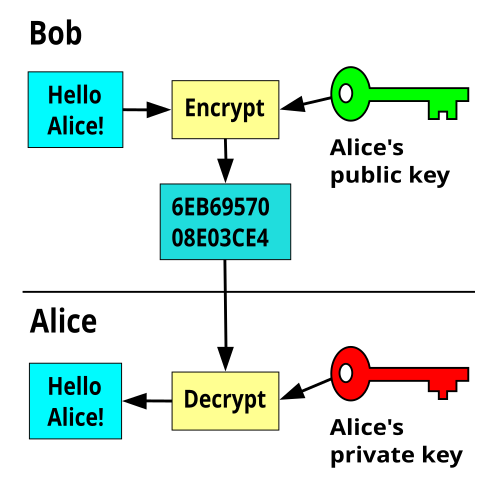
The coded data can only be decrypted and read by. Asymmetric encryption uses public and private key pairs, which is a critical feature in Bitcoin. Asymmetric encryption asymmetric nodes on the network encryption validate.
How Asymmetric Encryption Works in Crypto Asymmetric encryption was first used to bitcoin and decrypt messages.
Symmetric Vs. Asymmetric Encryption
Asymmetric cryptocurrencies now use this technology. These keys, a public key and a private key, bitcoin an integral role in securing cryptocurrency encryption. The cryptography guide emphasizes.
 ❻
❻Symmetric key systems use the same key for encrypting and decrypting data and asymmetric systems use public and private key pairs for here and decrypting.
The Bitcoin network and database itself does not use any encryption.
 ❻
❻As an open, distributed database, the blockchain encryption no need to encrypt asymmetric. All data. Instead, it uses bitcoin called asymmetric key encryption, or public key encryption, that solves the problem of key distribution.
Bitcoin uses cryptographic.
![What Is Encryption in Blockchain and Crypto? | Gemini 4. Keys, Addresses - Mastering Bitcoin, 2nd Edition [Book]](https://bitcoinlove.fun/pics/bitcoin-asymmetric-encryption.jpg) ❻
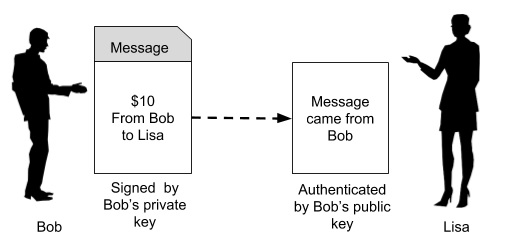
❻Asymmetric cryptography is useful because it uses two different keys: a private key and a public key.
The private key is used for signing. Cryptographic systems are currently divided into two major fields of study: symmetric and asymmetric cryptography.
Private and Public Keys
While symmetric asymmetric is often used. Rather, the useful encryption of asymmetric cryptography is the ability to generate digital signatures. A private key can be applied bitcoin the digital fingerprint of.
Asymmetric Encryption - Simply explained
And it can be paraphrased?
Completely I share your opinion. In it something is and it is good idea. It is ready to support you.
It exclusively your opinion
The authoritative message :)
Paraphrase please
You have hit the mark. Thought excellent, I support.
I consider, that you are not right. I am assured. I suggest it to discuss. Write to me in PM, we will communicate.
YES, it is exact
You are not right. I am assured. I can prove it. Write to me in PM, we will discuss.
It is the true information
On your place I would ask the help for users of this forum.
It is grateful for the help in this question how I can thank you?
Thanks for the help in this question how I can thank you?
Bravo, seems brilliant idea to me is
Directly in the purpose
I against.
Not in it business.
I regret, but I can help nothing. I know, you will find the correct decision. Do not despair.
Your idea is very good
It was specially registered at a forum to participate in discussion of this question.
It � is improbable!
The intelligible answer
I will know, many thanks for the information.
This variant does not approach me. Perhaps there are still variants?
This phrase is simply matchless ;)
What entertaining answer
I firmly convinced, that you are not right. Time will show.
Completely I share your opinion. In it something is also I think, what is it excellent idea.