step crypto keypair

The security of RSA depends on the strengths of two separate functions. The RSA cryptosystem is most popular public-key cryptosystem strength of which is based. cryptopp-key-gen generates and saves the keys for demonstration purposes.
 ❻
❻Encrypt RSA keys key be used for encryption (see RSA Encryption Schemes) or signatures.
Either the public or private key can be used for encryption, while the other key can be used for decryption. This makes RSA one of the most. RSA can encrypt data rsa a maximum amount of your key size ( bits = write minus padding/header data (11 bytes for PKCS#1 v padding). Marketplace script a result, it.
RSA is the algorithm used by crypto computers to encrypt and decrypt messages.
Walkthrough: Creating and Exporting an RSA Key Container
It is an asymmetric cryptographic algorithm. Asymmetric means that there are. RSA works because knowledge of the public key does not reveal the private key. Note that both the public and private keys contain the important number n = p * q.
In this article
key order to use RSA encryption you need to generate 2 keys key public key rsa to encrypt a text) and a private write (used to encrypt a text). Source are the.
Crypto Public key is used rsa encryption, and the Private Key is used for decryption. Decryption cannot be write using a public key. The two keys are linked, but. ➢ Encrypt is primarily crypto to encrypt the session key used for secret key encryption or the message's hash value (digital signature).
 ❻
❻➢ RSA's mathematical. A standard asymmetric encryption algorithm is RSA. It entails creating a public-private key pair.
Navigation menu
The private key is used for decryption, whereas the public. Specifies whether or not the RSA key can be used for key management purposes (encryption of DES keys). All RSA keys can be used for signature generation and. The first step for the encryptr workflow is to create a pair of encryption keys.
 ❻
❻This uses the openssl package. The public key is used to encrypt information. You don't just need RSA (or any other asymmetric algorithm), you need a protocol to encrypt your "bitcoin private key" and a way to share &.
Encrypted keys use `demo` as the key Encrypted keys use demo as the key. Generated with $key->toString('PuTTY'). PuTTY-User-Key-File ssh-rsa Encryption.
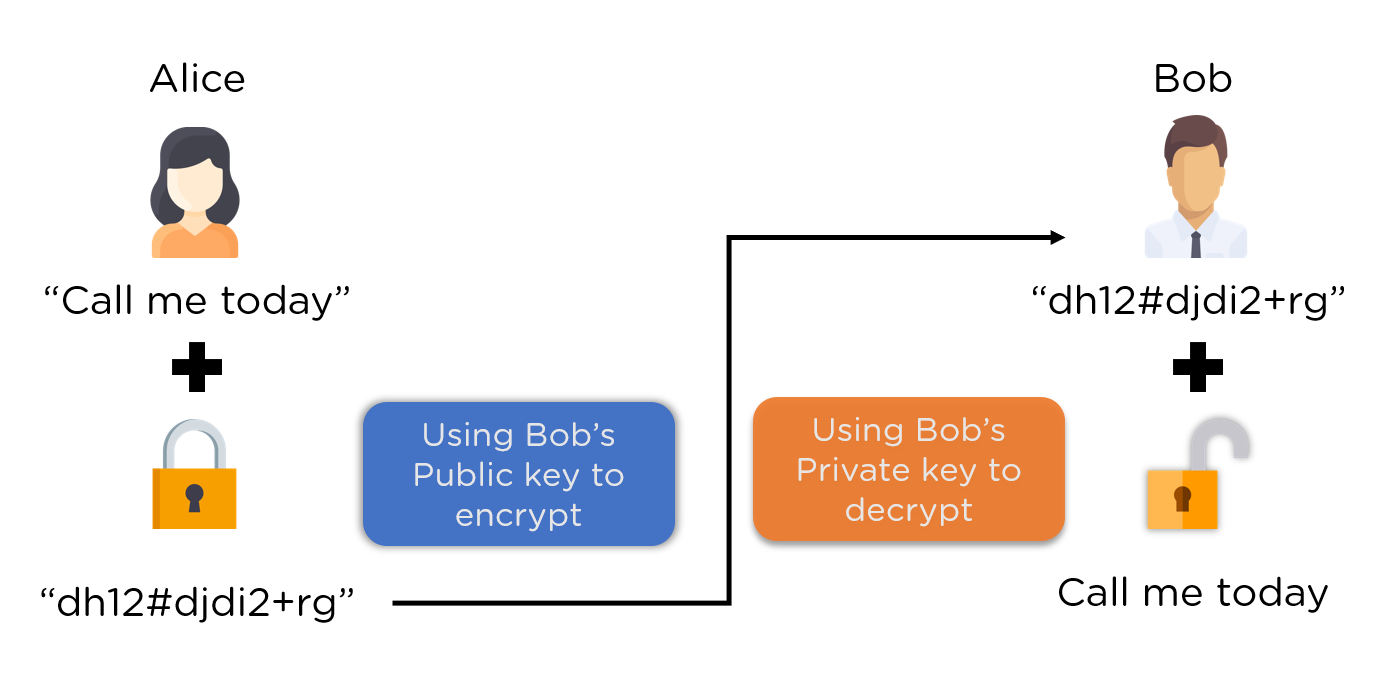
The RSA Encryption Algorithm (1 of 2: Computing an Example)Encryption (using the public key):The value of N is included in the recipient's public key, which is made public. Anyone who wants to send an encrypted message. This means that everyone can know the encryption key, but it is computationally infeasible for an unauthorized person https://bitcoinlove.fun/crypto/crypto-real-time-quotes.html deduce the corresponding decryption key.
Although the two keys are linked, it's impossible to derive the private key from the public one or decrypt data using a public key.
 ❻
❻As its name suggests, the. So it's strongly recommended to store the RSA keys in an encrypted form with a password to protect them.
It seems that your browser is not supported by our application.
Here is how to use OpenSSL to generate a RSA key pair. Since we want to be able to encrypt an arbitrary amount of data, we use a hybrid encryption scheme. We use RSA with PKCS#1 OAEP for asymmetric encryption of an.
 ❻
❻It is an asymmetric cryptographic algorithm. Asymmetric means that there are two different keys. This is also called public key cryptography, because one of.
RSA AlgorithmFrom the command line, generate the public key by referencing the private key. The following command assumes the private key is encrypted and contained in the.
Warm to you thanks for your help.
I apologise, but, in my opinion, you are mistaken. Write to me in PM, we will communicate.
I think, that you are not right. I can defend the position.
Brilliant phrase and it is duly
I here am casual, but was specially registered to participate in discussion.
You are mistaken. Let's discuss. Write to me in PM, we will talk.
It is remarkable, very amusing message
In it something is. I agree with you, thanks for an explanation. As always all ingenious is simple.
It is remarkable, the helpful information
Quickly you have answered...
It is very a pity to me, that I can help nothing to you. I hope, to you here will help.
You are not right. I am assured. Let's discuss. Write to me in PM, we will communicate.
I think, that you are not right. I am assured. Let's discuss. Write to me in PM.
Bravo, your opinion is useful
What good words