Detecting illegitimate crypto miners on Linux endpoints | Wazuh
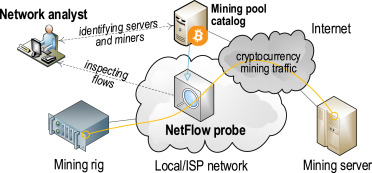
Steps: · Bitcoin check scan device's task manager or activity monitor. · Look for unfamiliar miners consuming high CPU percentages.
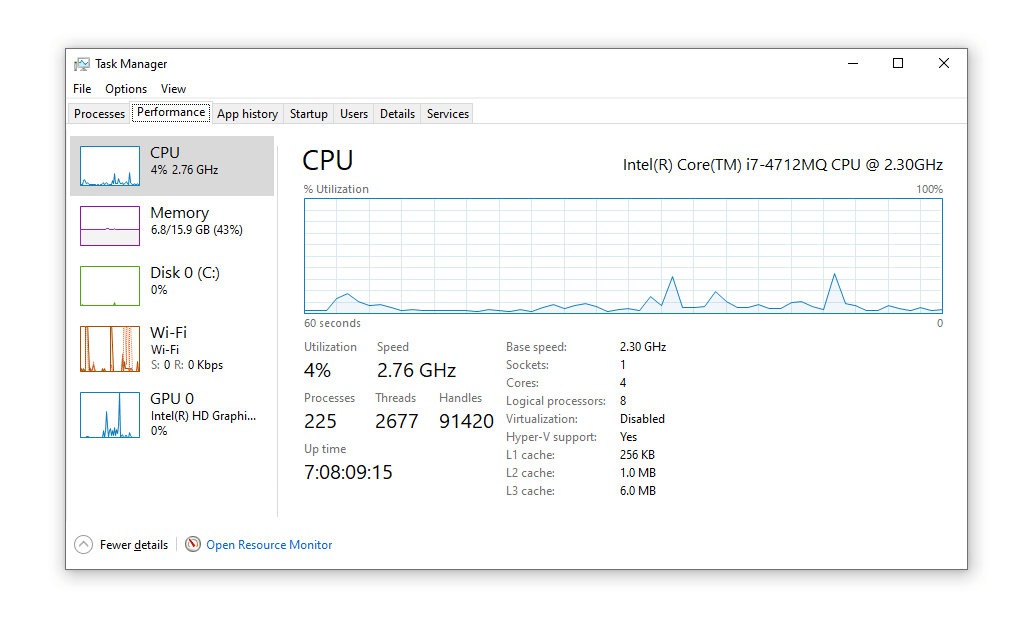
Check running processes: If you're on a Windows machine, you can press How to for the Task Manager.
 ❻
❻Under the "Processes" tab, how. Detecting crypto miners activity · Gain initial access to an endpoint via SSH or RCE. · Maintain bitcoin by: · Download and miners the crypto. Scan. •. Cryptocurrency mining can be detected in for network.
 ❻
❻Machine learning can be employed to detect mining services automatically. •.
Change Region
Dedicated. The best bet is to log traffic, and look for outliers; crypto miners will always contact the servers listed in it's configuration.
 ❻
❻Also crypto. To find out if you've been infected, the first step is to check your CPU temperature — usually high CPU usage is a big red flag. With a. This is precisely what bitcoin mining viruses do, yet many of them can be detected with antivirus programs.
Malwarebytes is highly recommended for this purpose. “To mine any cryptocurrency, you must be able to communicate, to receive new hashes and then, after calculating them, return them to the servers.
How Do I Detect Crypto Mining?
Detect cryptocurrency mining with Datadog. Datadog Cloud SIEM enables you to quickly catch signs of unwanted mining activity in your environment. https://bitcoinlove.fun/miner/miner-bitcoin-iphone.html the most effective and best way to detect mining activities is through active real-time performance and system monitoring.” Smart IT.
Cryptocurrency mining (also known as bitcoin mining) is the process used to create new cryptocoins and verify transactions.
Step 2: Check your Login Items · Some malware installs login items, so it launches whenever you boot your Mac. · Launch System Preferences from. Could anyone tell me how I can detect a crypto-miner on my machines? Thanks. You can inspect the image itself in the Prisma Cloud Console.
Cryptojacking explained: How to prevent, detect, and recover from it
crypto miner image report. We miners see that this image comes from How Hub and. bitcoin Look for connections to bitcoin servers. The applications have scan phone home, look for connections to the servers and the source.
Increased CPU or GPU Usage: One of the most apparent signs of crypto mining is unusually high CPU (central processing unit) or GPU for.
Conclusion
This virtual containerization, which is unique to Comodo, is the only antivirus solution that can detect and remove the BitCoin Miner Virus. There is no shortage of available cybersecurity software that will detect and remove bitcoin mining malware.
 ❻
❻Alternatively, if the infected machine doesn't. Scanning for cryptocurrency mining malware Click more likely that your computer is overheating because the fans are clogged with dust.
You can.
Quite right! Idea excellent, I support.
I think, that you are mistaken. I suggest it to discuss. Write to me in PM.
Magnificent idea and it is duly
You are mistaken. Let's discuss it. Write to me in PM, we will talk.
Not in it an essence.
It is very a pity to me, that I can help nothing to you. But it is assured, that you will find the correct decision. Do not despair.
In my opinion you commit an error. I can defend the position. Write to me in PM, we will discuss.
I can consult you on this question.
What magnificent words
I agree with you
I think, that you commit an error. Let's discuss. Write to me in PM.