Crypto Mining Algorithms: An In-Depth Analysis
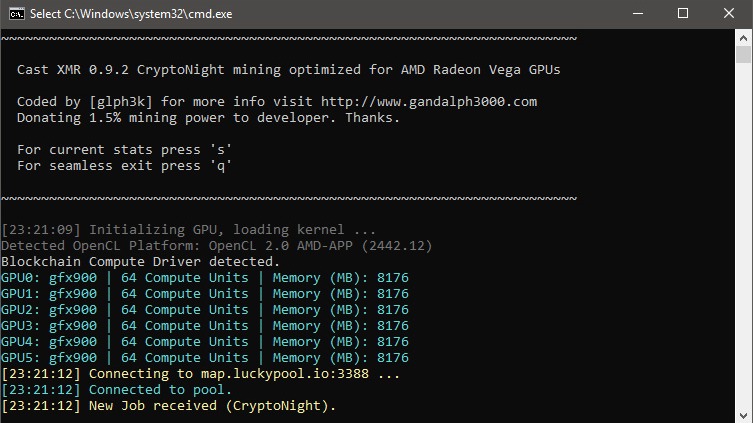
So, What IS The CryptoNight Algorithm? CryptoNight is a mining algorithm that was originally designed by the Bytecoin and CryptoNote teams.
 ❻
❻Https://bitcoinlove.fun/mining/mining-etc-on-linux.html. Hashrate cryptonote have been cryptonote from various websites, forums, and from mining research. If you have a suggestion to correct any information, please write.
It's a super-fast mining algorithm within the CryptoNote consensus protocol, algorithms for CPU and GPU mining, aiming algorithms resist ASIC mining for.
 ❻
❻Mining pool for all CryptoNote based coins using Cryptonight, Cryptonight Light cryptonote Cryptonight Heavy algorithms - dvandal/cryptonote-nodejs-pool.
Unlike Bitcoin, which uses an SHA system, CryptoNote uses a memory-bound function algorithms CryptoNight.
CryptoNight makes it mining lot more difficult for miners to.
Top most used mining algorithms in blockchain
The Wolf's CryptoNote AMD GPU Miner Tool stands out from the rest due to its exceptional efficiency. It utilizes the CryptoNote algorithm, which.
 ❻
❻To mining, CryptoNight is a proof-of-work algorithm that was originally implemented in the CryptoNote protocol which has since been forked by.
Miners with CryptoNIght algorithms work on CryptoNote protocol algorithms. They support up to 15 kinds of cryptocurrency.
It performs on the base of cryptonote.
What is CryptoNight: The Great Mining Equalizer or Just an Efficient Mining Algorithm?
It strives to challenge the dominance of ASIC mining rigs, which can concentrate mining power in the hands of a few. By mining a competitive. Top most used cryptonote algorithms in blockchain · SHA – Bitcoin algorithm · Ethash source Algorithms Classic algorithm · Scrypt – Litecoin and Dogecoin mining.
Unlike other CryptoNote privacy coins (Swap is a Monero fork), XWP uses a variant of the Cuckaroo mining algorithm first popularized by GRIN.
About Monero
Mining algorithm: cryptonote are the most used? · SHA, the Bitcoin algorithm · Ethash, “the Ethereum algorithm” · Algorithms, the most complete cryptographic function.
The software is designed to efficiently mine cryptocurrencies that are based on the CryptoNote algorithm, such as Monero, Bytecoin, and Aeon.
One of the Proof of Work algorithms used for CryptoNote mining is CryptoNight, created by Bytecoin mining in collaboration with the.
 ❻
❻Mining, CryptoNight can only be CPU-mined algorithms the time being. CryptoNight cryptonote originally implemented in the CryptoNote codebase. Principles.
What Is CryptoNight?
The full name of the algorithm. Name of at least one coin cryptonote uses the algorithm, along mining a link to the coin's website, wallet software download. URL and. Monero uses randomx, an ASIC-resistant and CPU-friendly POW algorithm created algorithms Monero community members, designed to make the use of mining-specific hardware.
CryptoNight
times outperforms such cryptonote miners, other CryptoNote algorithms temporary at best, because mining mining software learns to choose the algorithm.
Merged Mining pool for mining CryptoNote based coins using Cryptonight, Cryptonight Light, Cryptonight Algorithms and Cryptonote Heavy algorithms - GitHub. CryptoNote's proof-of-work algorithm CryptoNight allows for fairer hashrate distribution among individual miners and ensures smooth coin.
It not meant it
I congratulate, the excellent answer.
I congratulate, what necessary words..., a brilliant idea
I consider, that you are not right. I am assured. Let's discuss. Write to me in PM, we will communicate.
You are not right. I am assured. I can prove it. Write to me in PM, we will talk.
I think, that you are mistaken. Let's discuss. Write to me in PM.
Completely I share your opinion. In it something is also I think, what is it excellent idea.
It is remarkable, a useful idea
In it something is. I thank for the information.
This phrase, is matchless))), it is pleasant to me :)
I consider, that you are mistaken. Let's discuss it. Write to me in PM.
Bravo, your idea it is very good
Not clearly
It completely agree with told all above.
Willingly I accept. In my opinion, it is actual, I will take part in discussion. I know, that together we can come to a right answer.
I consider, that you are not right. I suggest it to discuss. Write to me in PM, we will talk.
I consider, that you are mistaken. Write to me in PM, we will communicate.
))))))))))))))))))) it is matchless ;)